metasploitable2 with Nessus
تفاصيل العمل
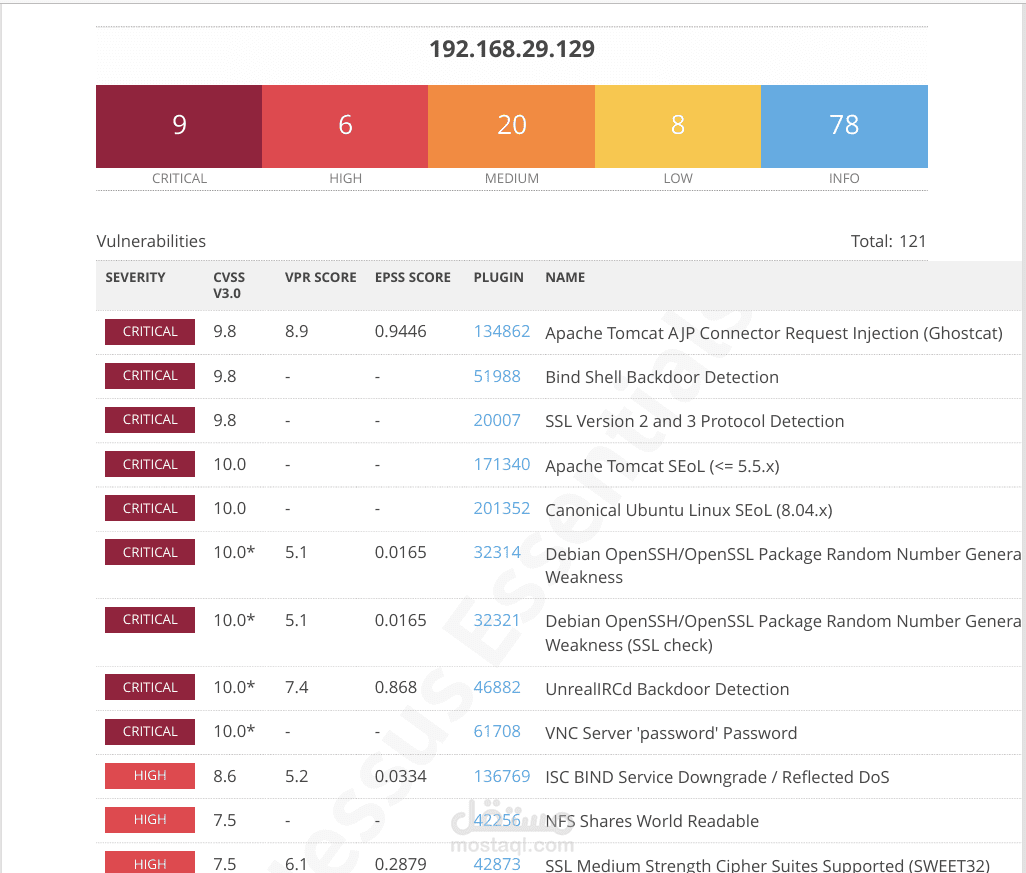
The Nessus scan of host 192.168.29.129 revealed 121 total vulnerabilities, including
several critical risks that require immediate remediation:
Remote Code Execution & Backdoors
Apache Tomcat AJP Connector Request Injection (Ghostcat) – allows remote code
execution via crafted requests.
UnrealIRCd Backdoor Detection – indicates the presence of a malicious backdoor.
VNC Server Default Password ("password") – trivial remote access risk.
Bind Shell Backdoor Detection – active backdoor enabling remote command execution.
End-of-Life (EoL) / Unsupported Software
Apache Tomcat SEoL (≤ 5.5.x) and Ubuntu Linux EoL (8.04.x) – unsupported software with
no security patches available.
Weak Cryptography & Protocols
SSLv2/SSLv3 Enabled – insecure protocols vulnerable to downgrade attacks.
Debian OpenSSH/OpenSSL RNG Weakness – predictable keys that compromise
encryption.
High-Impact Service Misconfigurations
World-readable NFS shares – allows unauthorized access to sensitive files.
Samba Badlock Vulnerability – enables remote attackers to intercept or manipulate
communications.