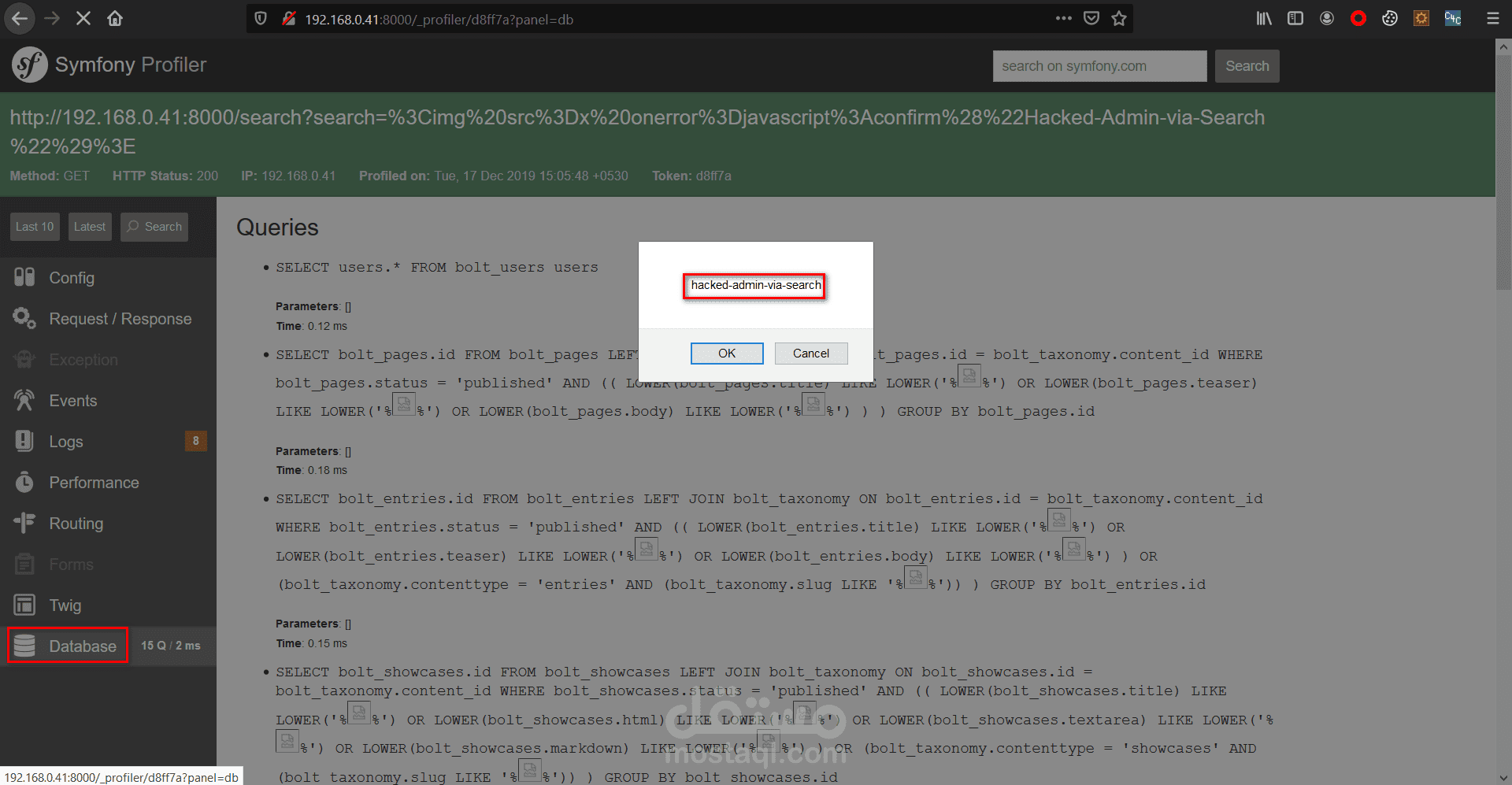
Stored XSS in User Profile Description
تفاصيل العمل
Type: Stored Cross-Site Scripting (XSS)
Severity: Medium
Summary:
While testing a production web application as part of a responsible disclosure program, I discovered a stored XSS vulnerability in the user profile section. The application allowed users to update their profile descriptions, but failed to sanitize input properly.
Steps to Reproduce:
Log in and navigate to the profile settings page.
In the "About Me" or description field, enter the following payload:
html
Copy
Edit
<script>alert('XSS')</script>
Save the profile and visit it as another user — the alert is triggered in their browser.
Impact:
An attacker could inject malicious scripts that steal session cookies, redirect users to malicious sites, or deface user-facing content.
Recommendation:
Implement proper input sanitization and output encoding, especially for fields that render HTML on the frontend.